
The research team at Safety Detectives has discovered a data leak, which potentially exposed over 10 billion records of an Ireland-based adult live-streaming website CAM4.com. The exposed database exceeded 7TB (terabytes) of information including its production logs. The researchers contacted CAM4 informing them of the data leak, and prompt response was received to secure the exposed database.
Data Leaked from the Adult Website
CAM4.com is owned by a parent company Surecom Corp., which has another adult website Smart-X.net registered under its banner. Researchers said that millions of leaked entries were unprotected and publicly viewable.

These exposed records consisted of both user and critical company information like personally identifiable information (PII) and production logs including:
- First and last names
- Login credentials
- Country of origin
- Sign-up dates and login logs
- Gender preference and sexual orientation
- Device information (MAC/IP addresses, OS details)
- User conversations
- Transcripts of email correspondence
- Password hashes
- Payments logs including credit card type, the amount paid and currency type
- Fraud/Spam detection logs
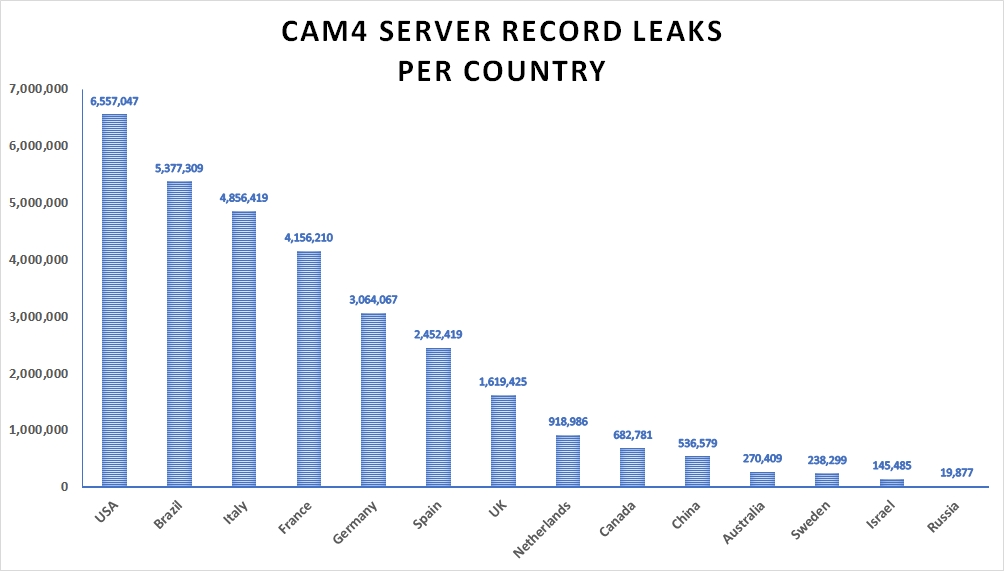
The log files revealed users’ password information, however, many sets of private information were incomplete, while password fields were masked in a majority of the instances investigated. Most of the users affected belonged to the U.S. followed by Brazil and Italy. It is difficult to gauge the precise number of records and their respective locations due to multiple duplications of entries, however, here is a country-by-country view of exposed email records:
Threat Summary |
|
| Website Name | CAM4.com (adult live-streaming website) |
| Threat type | Data leak |
| Affected Audience | Mainly U.S., Brazil, and Italy |
| Campaign Active Since | From at least March 16, 2020 |
| No. of Leaked Records | 10.88 billion including personally identifiable information (PII) |
| Leaked Server Info |
|
| Damages Caused | The leaked records are at risk of identity theft, financial fraud, phishing scams, and blackmail. Additionally, the leaked website’s backend data could be assessed to create a backdoor and exploit the website with further threats including ransomware attacks. |






















